use SSH tunnels to cross community boundaries
10 min read
The Safe Shell protocol defines a mechanism for securely connecting to a distant host. Initially, SSH was supposed to interchange Telnet, the unique web utility for operating distant login periods. However SSH has turn out to be far more than a instrument for terminal emulation, largely as a result of it supplies the means to securely route community visitors by way of ports and host techniques outlined by the consumer. These connections are referred to as tunnels as a result of they supply a connection by way of which safe community information may be transmitted over an unsecured community.
An SSH tunnel is a safe connection between an SSH consumer and an SSH server. Community visitors from the native machine is routed from an arbitrary specified port on the localhost by way of the SSH connection to a specified port on the distant machine.
For essentially the most fundamental use case, SSH is used to provoke a terminal session with a distant SSH server. As soon as the connection is made, the consumer can challenge distant instructions on that server. When the safe connection makes use of distant port forwarding, nonetheless, the SSH tunnel supplies a way to tunnel by way of personal networks and the firewalls that shield them.
This tutorial exhibits how you can use SSH tunnels for 3 particular functions:
- Entry a restricted web useful resource from inside a firewall utilizing SSH port forwarding.
- Arrange a SOCKS proxy server for the native machine.
- Arrange an SSH reverse tunnel to bypass firewall safety to entry an SSH server inside a personal community.
SSH is a vital instrument utilized by networking and data safety professionals — in addition to by hackers and different attackers. Earlier than experimenting with SSH on a corporation’s community, you’ll want to verify in with the IT division to find out whether or not SSH tunneling is permitted — and to make it possible for the experiments don’t set off cybersecurity alarms.
Getting ready to arrange an SSH tunnel
This tutorial focuses on utilizing the OpenSSH implementation of the SSH protocol on the command-line interface (CLI). Though GUI implementations of SSH, corresponding to PuTTY for Home windows, exist, trendy OSes nearly universally embody CLI implementations of SSH, together with OpenSSH on Home windows variations 10 and later, macOS and Linux.
Earlier than making an attempt to open an SSH tunnel, take the next steps:
- Confirm that SSH is put in and operating on the native machine, in addition to on the distant SSH server. On Home windows techniques or Unix-based techniques, this may be executed by opening a PowerShell window (Home windows) or a shell session (Unix-based techniques) and coming into the ssh With none parameters, the command returns a message indicating appropriate utilization and accessible parameters.
Additionally, confirm that the SSH server sshd is operating on whichever host goes for use for SSH entry. If the host doesn’t have a daemon (server program) for the SSH server operating and listening for requests to open an SSH connection, it must be began earlier than a tunnel may be created. One technique to confirm that is to provoke an SSH reference to the server in query. If the connection is accepted, then it’s protected to imagine that sshd is operating.
That is additionally a very good time to confirm that the consumer account getting used on the SSH servers has the right permissions. At a minimal, the consumer account needs to be licensed to challenge superuser instructions — utilizing the sudo command — however with limitations to stop the account from being hijacked and used in opposition to the group.

Working the ssh command to confirm SSH is put in on Home windows system
- Get or confirm the hostname or the IP deal with of the distant server. The server IP deal with is all the time adequate, though having the area title could make coming into SSH instructions simpler.
On Home windows techniques, the IP deal with of the system may be decided by way of the Settings utility, underneath the Community & Web choice, by viewing the Properties of the community interface that’s presently linked to the web.
Instructions for locating the IP deal with utilizing the command line can be found for all OSes:
- On Home windows techniques on the command line, the IP deal with of the system may be decided by coming into the PowerShell command ipconfig that shows the community configuration, together with IP deal with, for all community interfaces on the system.
- On Linux techniques, corresponding to Unix-based OSes, which incorporates macOS, the IP deal with may be decided by coming into the Unix command ifconfig that shows the community configuration, together with IP deal with, for all community interfaces on the system.
Discovering a Linux host’s IP deal with utilizing the ifconfig utility
- Decide the port numbers for use for redirection with SSH port forwarding. For ports assigned to be used with particular protocols, often known as well-known ports, discuss with the Web Assigned Numbers Authority (IANA) Service Title and Transport Protocol Port Quantity Registry. Probably the most generally used IANA-registered ports embody port 80 (HTTP), 443 (HTTPS) and 22, which is the default port for utilizing SSH.
Typically, any non-well-known port, within the vary from 1024 to 65535, can be utilized — however port 1080 is the registered port for SOCKS and needs to be used when organising a dynamic port forwarding tunnel for use as a SOCKS proxy.
When organising a tunnel for native port forwarding, for instance, from an online server on the interior community to an exterior server, the supply port and vacation spot port may each be set to 80 for HTTP transmissions. When organising a tunnel on a neighborhood server that’s operating each as an SSH server and an online server, the inbound port could possibly be set to 8080 to distinguish tunnel visitors from atypical internet visitors.
- Assessment the deliberate tunnel earlier than implementation, and ensure all hosts concerned are reachable from related techniques. Issues to verify earlier than deploying the tunnel embody the next:
- Are the hosts reachable?
- Do all hosts have up-to-date and interoperable variations of SSH put in?
- Do hosts performing as SSH servers have the SSH server software program put in?
- Does the consumer have sufficient permissions on related techniques?
As soon as tunnel endpoints are outlined, taking a step-by step strategy may also help simplify troubleshooting since every part of the tunnel may be examined as it’s turned on.
- Initialize the SSH daemon on any system performing as a server. This will likely require a separate set up on some OSes. For Home windows — model 10 and later — a separate OpenSSH server executable have to be put in and initiated by the operator utilizing a PowerShell command line operating with Administrator permissions. The next command can be utilized to initialize an put in OpenSSH server daemon from the PowerShell command line:
PS C:Userspeter> Begin-Service sshdThe next command can be utilized on Ubuntu techniques to start out the OpenSSH server:
$ sudo service ssh beginThe sudo command requires coming into a certified password to achieve superuser entry to run the server service.
As soon as connectivity is established to all endpoint techniques and permissions for entry to SSH packages are confirmed, organising the tunnel is normally easy. Some SSH implementations could have totally different choices accessible, nonetheless. To find out which model of SSH is put in on Home windows, open a PowerShell window, and enter the next command:
PS C:UsersuserID> ssh -V
Checking model info for SSH in Home windows PowerShell
To confirm the model of SSH operating on Linux, enter the next command:
$ sudo service ssh begin
Checking model info for SSH utilizing -V choice in Linux shell
arrange a SOCKS proxy server
Some of the sensible functions of SSH tunneling, a SOCKS proxy is a tunnel that permits a bunch inside a personal community, protected by a firewall, to freely entry community assets on the worldwide public web. SOCKS proxies supply a simple technique to shield community communications with no VPN.
When used with SSH, SOCKS permits routing all community visitors from the native system by way of the safe SSH tunnel. This kind of tunnel is usually referred to as dynamic port forwarding as a result of it depends on SOCKS’ potential to direct community visitors from any port on the native system to any port on any distant system.
Use the next command to provoke a SOCKS proxy over an SSH tunnel on a Linux system utilizing the SSH server ssh-server.instance.com and consumer account peter:
$ ssh -D 1080 [email protected]
The -D choice — for dynamic utility port forwarding — permits SSH port forwarding for all ports, out and in. On this instance, the -D choice identifies port 1080 because the port on the native host for use to pay attention for tunnel visitors. It additionally permits SSH to handle task of utility ports, in order connections are established by way of the tunnel, SSH operates as a SOCKS proxy server. Any community utility being tunneled by way of the SOCKS proxy have to be configured to speak on this port, relatively than on the well-known ports used for the applying.

SOCKS proxy configuration in internet browsers is nicely documented and included within the browser configuration settings, as proven on this screenshot. Different functions could require modifications to a config file to direct the applying program to entry the proxy. Alternatively, SOCKS proxies may be configured on the OS stage — for instance, in Home windows Settings — so all community functions use the proxy.
The localhost serves because the proxy: It accepts community visitors to be tunneled on the specified port — 1080 for SOCKS — and the SOCKS host as localhost.
The command listed above may be refined. For instance, the next command makes use of the identical port, consumer account and distant host however provides choices:
$ ssh -D 1080 -C -N [email protected]
The -C choice permits compression for higher efficiency on a gradual community — though, on quick networks, this selection could cut back efficiency.
The -N choice specifies that distant instructions shouldn’t be run from the session. This permits a neighborhood operator to provoke port forwarding with out enabling any instructions to be run on the distant server.
As soon as the dynamic port forwarding tunnel is opened and the native pc is configured to make use of a SOCKS proxy, tunneled community visitors is forwarded to the general public web by way of the tunnel.
arrange an SSH port forwarding tunnel
Native port forwarding permits the native operator to bypass any firewalls or filters to entry an exterior server from inside a personal community. With native port forwarding, the native machine doesn’t have direct web entry, and the SSH server, which is straight reachable by the native system, does have web entry.
The connection between the native system and the SSH server is secured with authentication upon creating the SSH session, and formally designated SSH servers used for port forwarding are normally deployed with extra safety measures for a hardened server configuration.
The SSH circuit connects the SSH course of operating on the native pc with a distant course of. The distant course of is the server or useful resource on the exterior host, outdoors the protected community. The SSH consumer software program listens regionally for makes an attempt to entry the port related to the distant useful resource. When the SSH consumer software program receives information on that port, it forwards it by way of the encrypted and authenticated circuit to the SSH server. The SSH server then forwards that visitors to the supposed vacation spot.
The command to create a neighborhood port forwarding tunnel makes use of the next syntax:
$ ssh -L local_port:remote_destination:remote_port [email protected]_server
The -L choice is used to bind a port on the native machine with a distant port on the distant vacation spot IP deal with. The port is certain by way of the connection to the consumer account on the ssh_server.
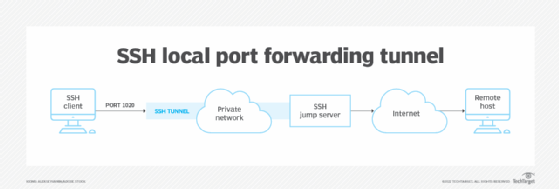
This diagram exhibits a bunch on the personal community sending community visitors to the native port 1020. That is the place the SSH consumer software program is listening for outgoing visitors. The SSH consumer then encapsulates that visitors to be forwarded by way of the prevailing SSH reference to the leap server.
The leap server is an SSH server that has been designated for “leaping” from throughout the personal community to the web. Bounce servers are normally hardened and are normally configured to require an SSH key file for authenticating every consumer.
This tunnel may be created for the consumer account peter on the SSH server named ssh_server.instance.com with the next command:
$ ssh -L 1020:www.instance.internet:80 [email protected]_server.instance.com
The leap server forwards community visitors from the SSH consumer to the distant useful resource being requested. Replies from the distant assets reverse the visitors by way of the web to the leap server, which then forwards the replies to the native operator.
arrange an SSH reverse tunnel
Reverse tunneling, often known as distant port forwarding, opens a tunnel by way of which an operator with entry to an SSH server may entry a bunch inside a personal community. Reverse tunnels are sometimes used to bypass firewalls to achieve entry to community assets inside personal networks — for instance, by attackers and penetration testers.
The command to create a neighborhood port forwarding tunnel makes use of the next syntax:
$ ssh -R remote_port:localhost:local_port [email protected]_server
The -R choice is used to bind a port on the distant machine with a port on the localhost. The port is certain by way of the connection to the consumer account on the ssh_server.
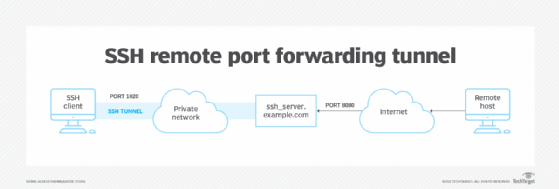
A reverse tunnel may be created with the consumer account peter on the SSH server named ssh_server.instance.com with the next command:
$ ssh -R 8080:localhost:1020 [email protected]_server.instance.com
On this tunnel, the SSH server ssh_server.instance.com forwards any community visitors it receives on port 8080 to the localhost course of listening for port 1020. This implies anybody with entry to the SSH server can hook up with the native machine.




.png)
